Office Building Time Attendance access control solution
DOWNLOAD
Chapter 1 :Proposal of the plan of using office access control solution
The endless salesmen interrupt your normal work order.
Employees leave their jobs without permission during working hours.
Unauthorized people break into your office rashly.
Unidentified people walk into your office and take away important documents from your desktop.
There are so many doors in the company that you have to carry heavy keys.
Unauthorized use of venues such as multi-purpose conference halls.
Unauthorized access to important places such as the financial room.
etc… …
Are you troubled by some tedious daily administrative affairs? The intelligent inductive IC card access control management system can help you solve some tedious problems in daily office, improve work efficiency, improve the working environment, and allow you and your colleagues to work in a safer and more orderly environment. Life.
Chapter 2 Overview of Access Control System Design Principles and Normative Basis
2.1 System overview
With the vigorous development of high technology, intelligent management has entered people's social life, and intelligent buildings have been erected to meet the needs of the information age. As a building and office environment used across the century, it must be functionally Meet the needs of current and future development and become a base for cultural and economic development.
The inductive IC card access management control system (referred to as access control system) has various functions such as door access control, real-time monitoring, security and anti-theft alarm. It mainly facilitates the access of internal employees and prevents outsiders from entering and leaving at will. The internal security has also been enhanced to provide users with an efficient and cost-effective working environment.
2.3 Main Design Basis Specifications
1. "International Integrated Wiring Standard" ISO/IEC11801
2. "Code for Electrical Design of Civil Buildings" JGJ/T 16-92
3. "People's Republic of China Security Industry Standard" GA/T74-94
4. "People's Republic of China Public Safety Industry Standard" GA/T70-94
5. "Technical Specification for Monitoring System Engineering" GB/50198-94
2.4 The name of the department recommended to use the access control function
Departments that recommend the use of inductive IC card access control systems:
Company gate, financial room, chairman, general manager, deputy general manager's office, data room, development department, warehouse, computer room, conference room, etc.
Other departments considering the use of proximity IC card access control systems as needed:
Administration Department, Engineering Department, Human Resources Department, Sales Department, Planning Department, etc.
Chapter 3 Identification Mode Function of WGACCESS Access Control System Function and Features of Recommended Brand Products in This Program
3.1 Identification Mode
Mode 1: One-way induction mode (card reader + controller + exit button + electric lock)
The user presents the authorized induction card outside the door, and after the card reader recognizes and confirms the legal identity, the controller drives to open the electric lock to release, and records the time of entering the door. Press the door open button, open the electric lock, and go out directly.
It is suitable for environments with general security level and can effectively prevent illegal entry of foreign personnel. is the most commonly used management mode.
Mode 2: Two-way induction mode (card reader + controller + card reader + electric lock)
The user presents the authorized induction card outside the door, and after the card reader recognizes and confirms the identity, the controller drives to open the electric lock to release, and records the time of entering the door. When the user leaves the controlled room, the authorized induction card must also be presented in the door. After the card reader recognizes and confirms the identity, the controller drives to open the electric lock to release, and records the time of going out.
It is suitable for environments with high security levels, which can not only effectively prevent the illegal entry of outsiders, but also query the last person and time to leave, so as to facilitate the implementation of responsibility and provide evidence in a specific period (such as theft).
Mode 3: Card + Password Mode
After swiping the card, you must enter the correct password to open the door. The password is a personalized password, that is, one person, one password. The advantage of this is that it is used for higher security occasions, even if the card is picked by someone, it cannot be entered, and the correct password needs to be entered. And it is easy to set the mode. For example, for the same door, some people must have a card + password to be allowed to enter, some people can swipe the card and can enter without a password, and the person with the highest authority can enter the super pass password.
Mode 4: card number + password mode
The user enters the correct card number and password on the card reader keyboard in sequence according to the format of *card number*password#, and then opens the door. This mode is the same as the card + password mode, and is also suitable for places with higher security; and there is no need to bring a card. For example, if the employee forgets to bring the card, the door can be opened after entering the card number and password, and the controller will store the entry and exit records.
Mode 5: Biometric Mode
A fingerprint reader or face recognition (international standard wiegand26 protocol) reader is installed at the door in combination with the controller to achieve a more secure biometric verification mode. Only when the authorized person presses the fingerprint or the designated person is present and the face scan match is successful, the door can be opened. This method is suitable for occasions with very high security level requirements, such as the company's financial department.
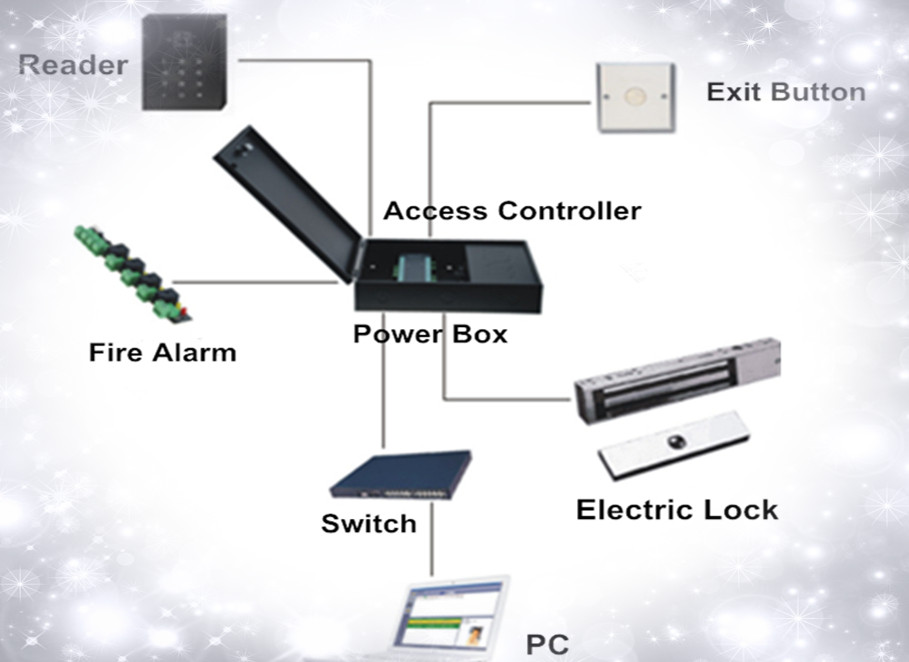
Chapter 4 Basic Components of WGACCESS Access Control System Functional Principle Topology Diagram and Configuration
4.1 The basic components of the access control system